How do I correlate user activity across multiple alerts in Panther?
QUESTION
How do I correlate user activity across multiple alerts?
ANSWER
It's common for a single behavior to create multiple alerts within one or more log types. You can search across data in Panther using Search or Data Explorer.
In Search, you can look for the username or email in p_any_usernames:
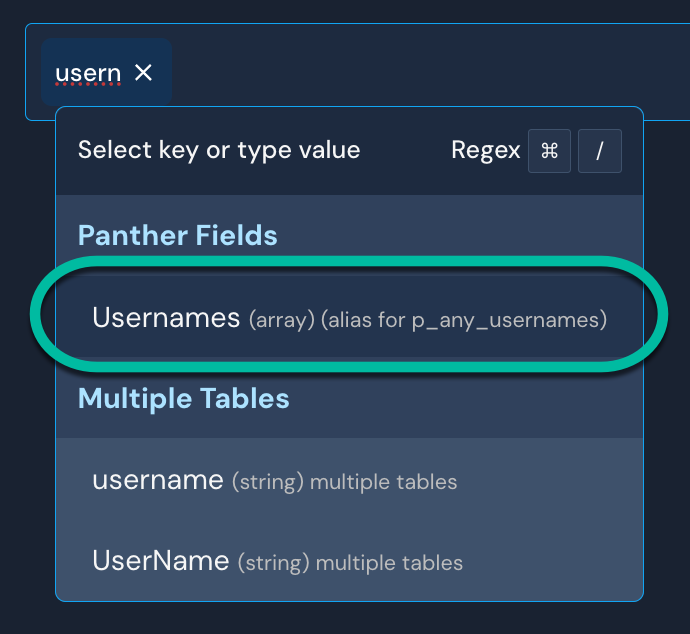
The steps below demonstrate an example of correlating alerts in the Data Explorer for CloudTrail.
- While viewing an alert in the Panther Console, copy the username from either the event itself or the alert title (as shown below):
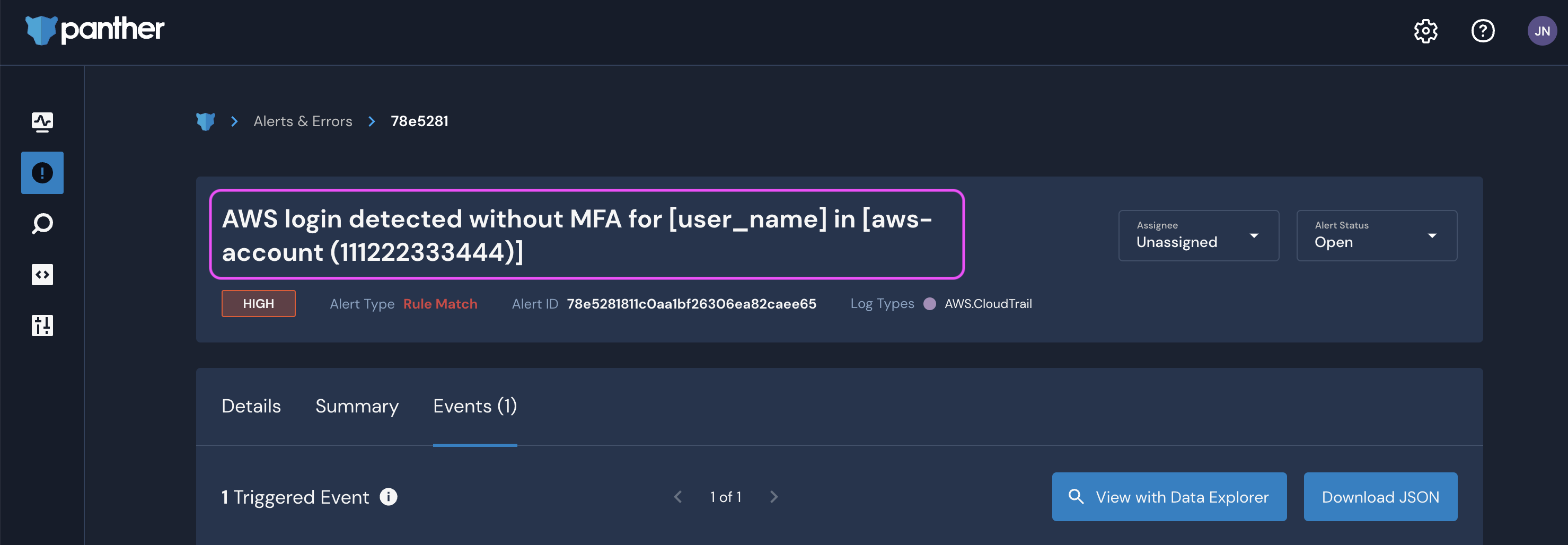
- Click View with Data Explorer to open a new page with the pre-populated query:
SELECT * FROM panther_rule_matches.public.aws_cloudtrail t WHERE t.p_alert_id='78e5281811c0aalbf26306ea82caee65' AND (p_alert_ update_time between '2022-10-14 15:33:072' AND '2022-10-14 15:33:08Z') LIMIT 100
- Keep track of the bolded fields above.
- Remove the Alert ID (
WHERE) clause - Modify the timeframe to query events within several hours before the alert firing
- Add an (
AND) clause for the username to correlate againstSELECT * FROM panther_rule_matches.public.aws_cloudtrail WHERE p_event_time between '2022-10-14 12:33:00Z' AND '2022-10-14 15:33:08Z' AND userIdentity:arn = 'arn:aws:iam::111222333444:user/user_name'
The resultant logs can then be further filtered and summarized to investigate activity across all CloudTrail logs.
Additionally, the following SELECT statement can speed up analysis by presenting important CloudTrail-specific fields:
SELECT p_event_time, p_rule_id, p_rule_severity, eventName, eventSource, requestParameters, errorCode, userIdentity FROM panther_rule_matches.public.aws_cloudtrail WHERE (p_event_time between '2022-10-14 12:33:00Z' AND '2022-10-14 15:33:08Z') AND userIdentity:arn = 'arn:aws:iam::111222333444:user/user_name' ORDER BY p_event_time ASC

